IEEE PAINE 2020: Decoding & Defending the Trusted Platform Module Against Malicious Hardware Implants
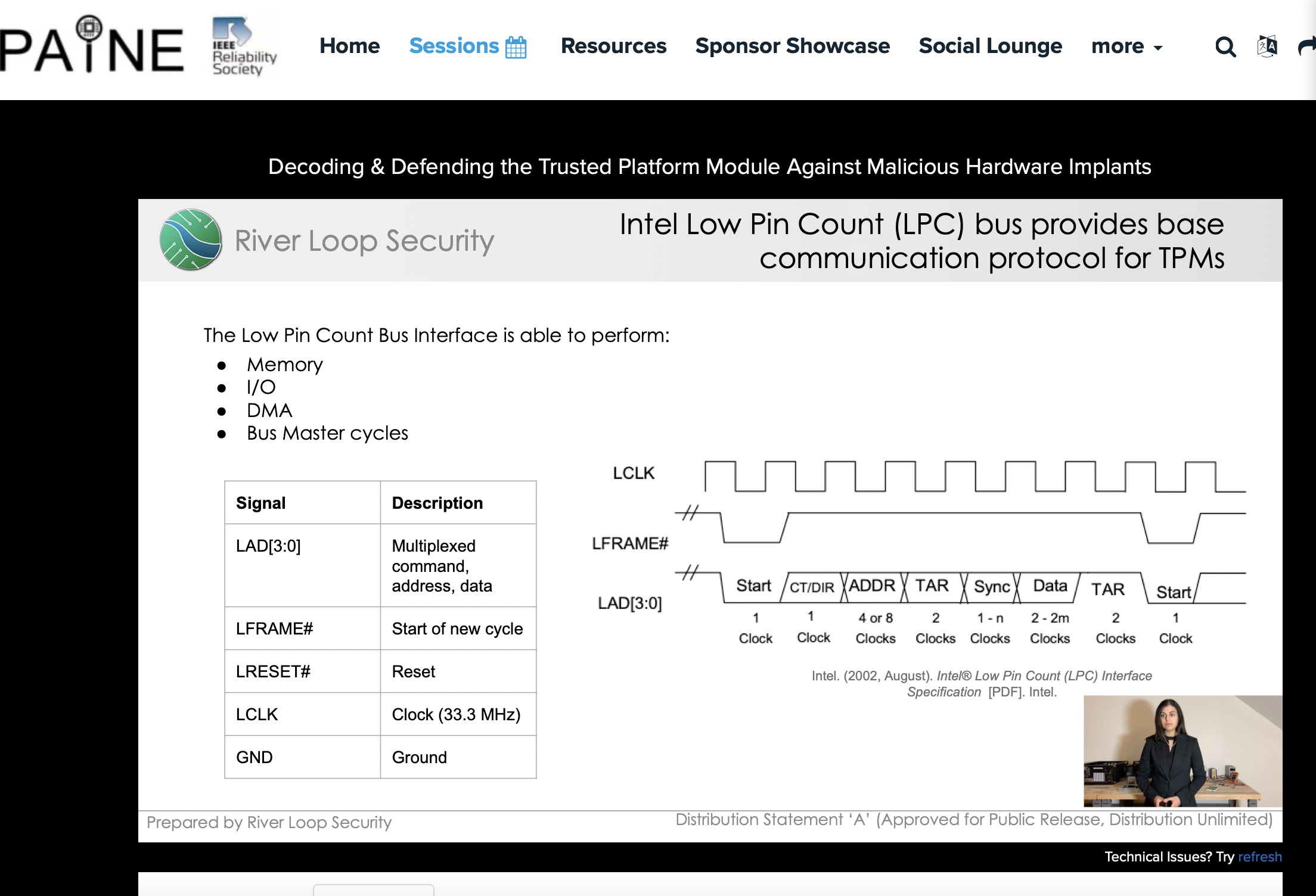
River Loop Security’s team members presented at IEEE International Conference on Physical Assurance and Inspection of Electronics (PAINE). The presentation provided a background on hardware implants, secure boot, and background on the Trusted Platform Module (TPM). We then focused on explaining and demonstrating our team’s work developing an TPM interposer and decoder. It concluded in discussing defending agaisnt malicious hardware implants.